Policy filter parameters
Policy filter parameters
License Family
License Family
Excludes packages with the specified license family.
| Comparators | Options |
|---|---|
isis not | AGPLAPACHEBSDCCGPLGPL2GPL3LGPLMITMOZILLANoneOTHERPSFPublic-Domain |
CVE Score
CVE Score
Excludes packages with the specified CVE score.
| Comparators | Options |
|---|---|
Greater thanGreater than or equal to | 1-10 |
CVE Status
CVE Status
Excludes packages that are associated with a CVE that has the specified status.
| Comparators | Options |
|---|---|
isis not | ActiveReportedMitigatedClearedDisputed |
Keep in mind that packages can be associated with multiple CVEs.
Package Age
Package Age
Excludes packages with the specified package age.
The package age is calculated based on the date the package was last updated.
| Comparators | Options |
|---|---|
Greater thanGreater than or equal to | Value: Enter a number Unit: days, months, or years |
Platform
Platform
Excludes packages with the specified platform.
| Comparators | Options |
|---|---|
isis not | linux-32linux-64linux-armv6llinux-armv7llinux-ppc64linux-ppc64lelinux-s390xnoarchosx-64win-32win-64zos-z |
Conda Spec
Conda Spec
Excludes packages with the specified conda spec.
Creating a policy filter
- From the Channels page, click Create under POLICIES.
- Provide a unique name for your policy. We recommend naming it something descriptive.
- In the Exclude package if section, click Add filter.
- In the FILTER GROUP section that appears, set filter parameters for packages you want to exclude.
-
Click Add Filter to Group to include additional parameters for this filter group, or click Add filter to add a separate filter for this policy.
Filters can be applied using either
andororlogic. Click the operator to toggle between the two options.This operator can greatly impact which packages are excluded.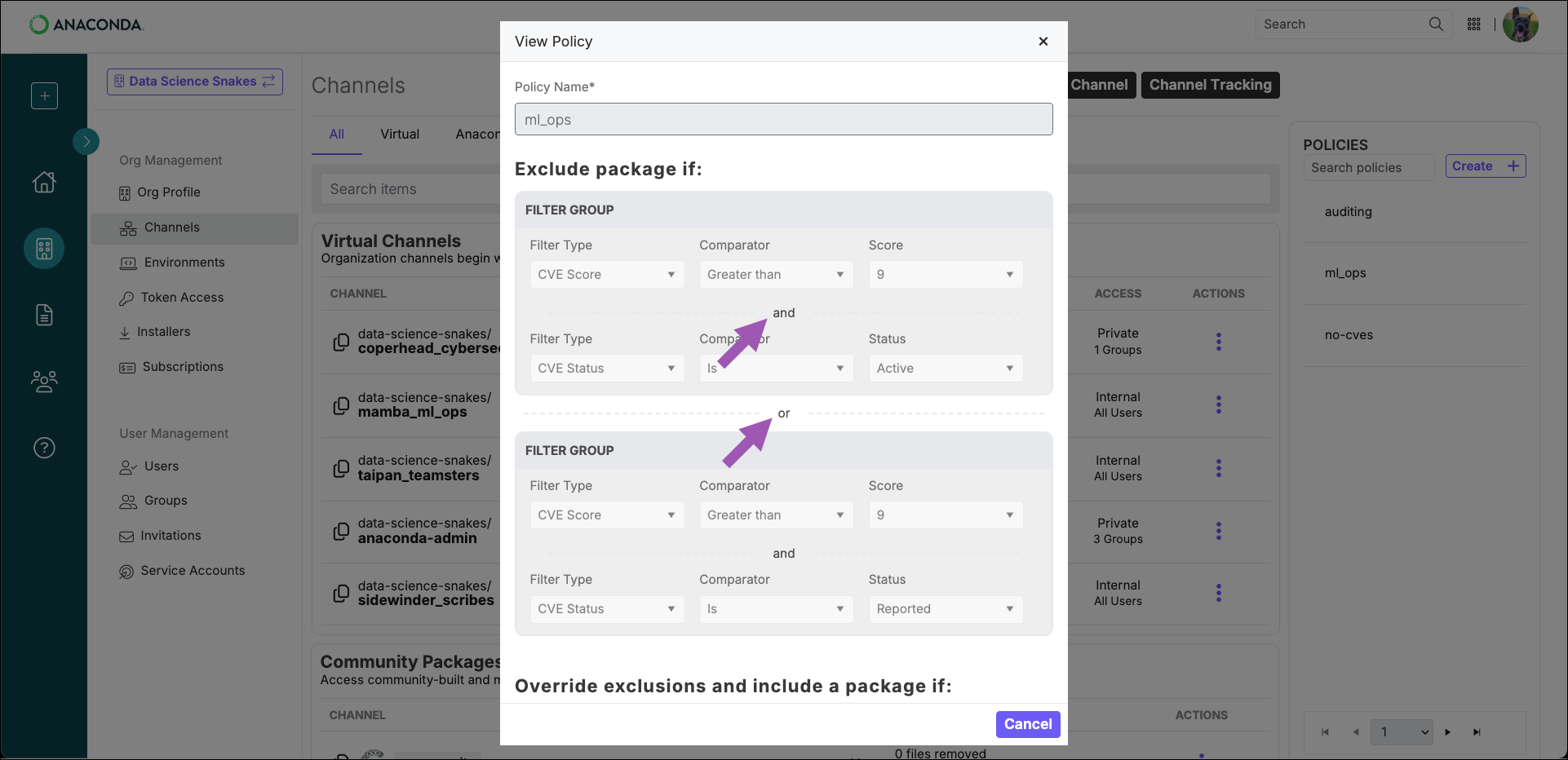
- Using the
andoperator means that all filter parameters must be met by a package for it to be excluded. - Using the
oroperator means that at least one filter parameter must be met by a package for it to be excluded.
anda Platform of linux-64 excludes linux-64 packages that have a CVE score greater than 7.However, a filter that excludes packages with a CVE score greater than 7ora Platform of linux-64 excludes:- All packages that have a CVE score greater than 7
- All linux-64 packages
- Using the
- Repeat this process to apply further package filtering preferences.
-
If necessary, in the Override exclusions and include a package if section, click Add filter.
In some cases, the exclusion parameters of a policy filter might inadvertently remove packages (or dependencies) that are critical for production projects. The override filter allows administrators to add these specific packages back to the channel.You can apply overrides using conda spec and CVE Status.
Example policy filter
Let’s say you want to exclude packages that have a CVE score greater than 7, unless the package file is associated with a CVE that has a Cleared status. Your policy filter would look like this: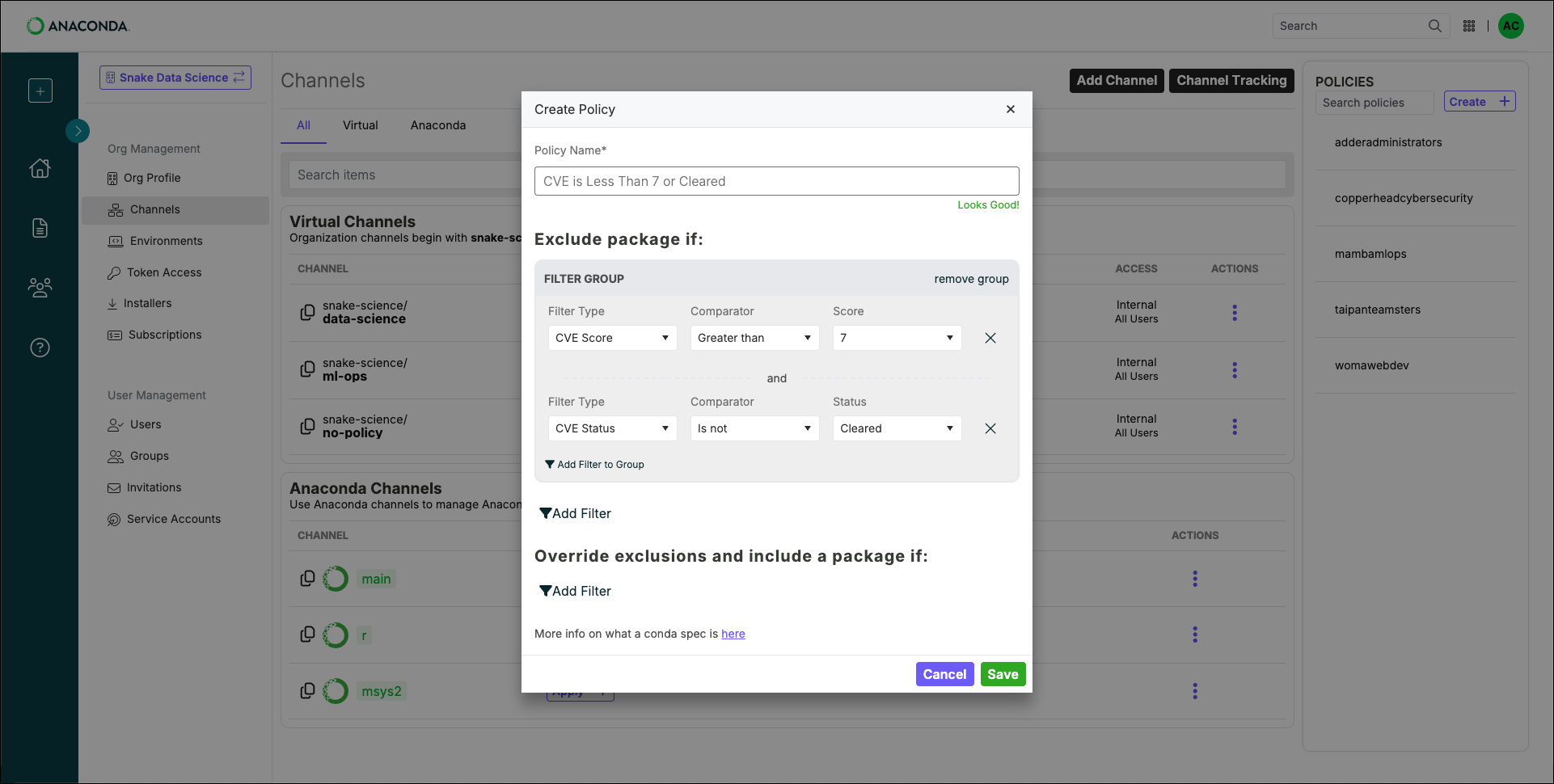
Applying a policy filter
Applying a policy filter to a channel restricts the packages that are able to be sourced from it.- From the Channels page, click Apply beside a channel’s name.
- Select a policy to apply to the channel.
- Click Apply to confirm.
- In Queue
- In Progress
- Completed
- Scheduled
Remove the policy filter by clicking Remove Policy beside the policy name in the channel list.
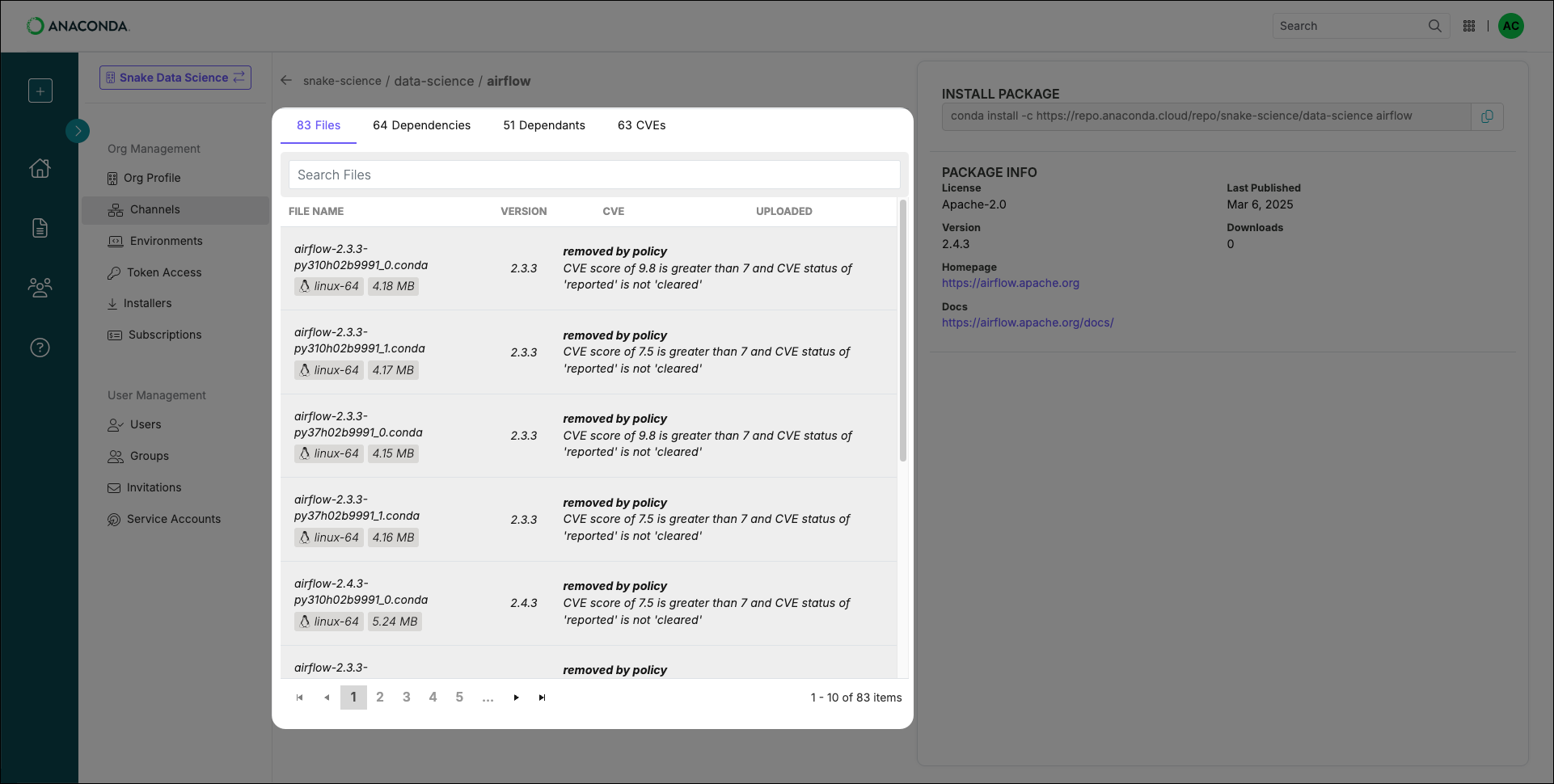
Removed files are not grouped, and some packages have multiple pages of files. For packages with many files, it is best to use the search box to narrow results.
Editing a policy filter
- Select the policy name from the POLICIES list.
- Change the parameters of the filter as if you were creating a policy.
- Click Save.
A warning displayed beside your filter indicates that it has become deprecated. Deprecated filters still work, but Anaconda recommends you update your policies to no longer use these filters.
Viewing the policy report
Once you have applied a policy filter to a channel, view the Policy Report to see a breakdown of the number of package files across various platforms that have been removed, and how many remain. From the Channels page, click the POLICY RESULTS for any channel to open the Policy Report.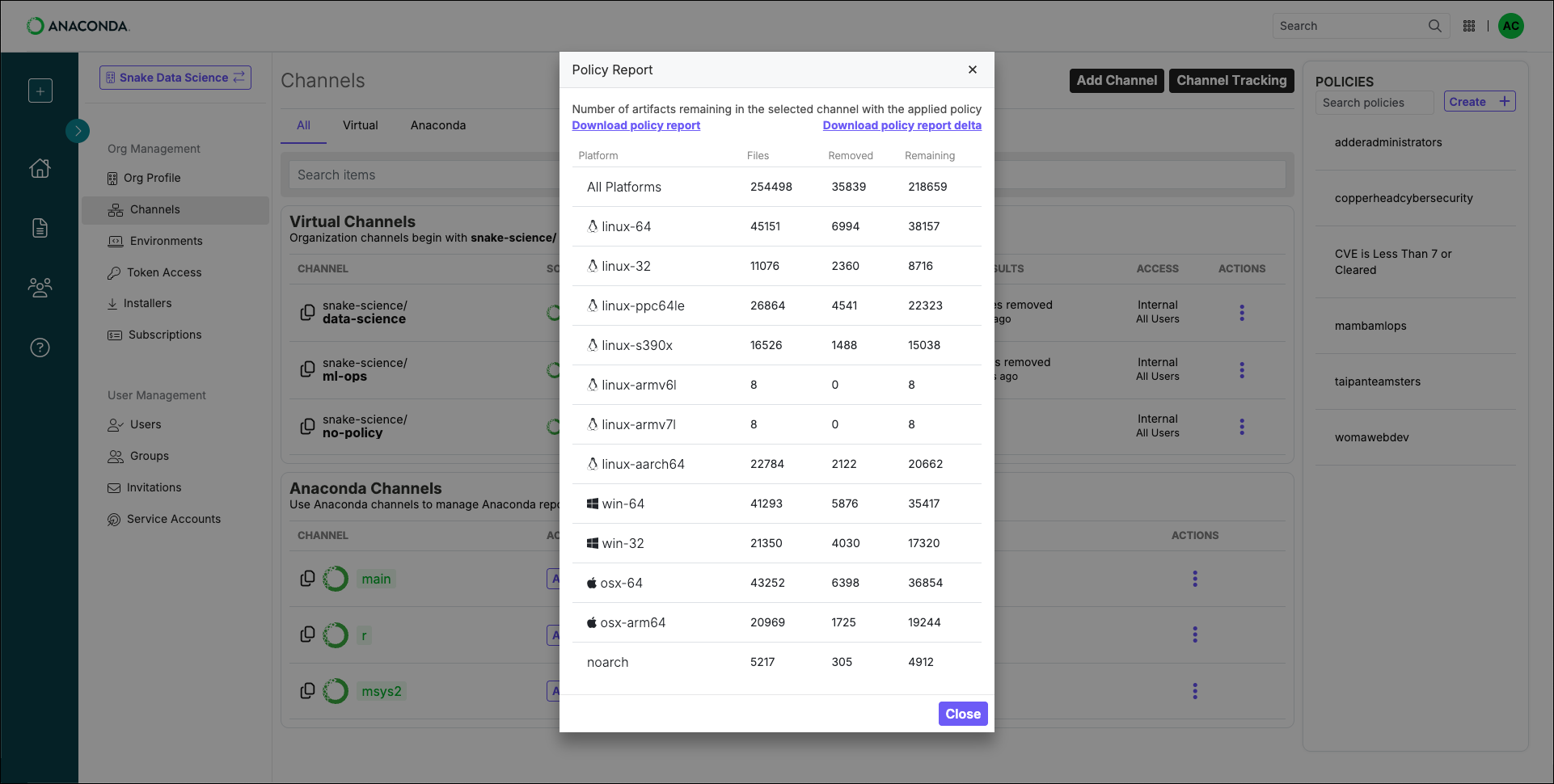
From here, you can download the policy report or the policy report delta in
.csv format.Policy deltas
Policy filters, once applied to a channel, run every four hours. Sometimes, due to newly reported CVEs or an updated CVE score or status, the contents of your channel will change when the filter performs its scheduled run. A package may become available that was not available previously, or you could find that a package you’ve been using is removed from your channel! From the channel details page, select View Policy Deltas to view a list of deltas. Deltas are the recorded changes to your channel’s contents. Policy delta history begins from when you first applied the policy to the channel. Once the policy is removed from the channel (if you need to edit it, for example) the policy delta history is lost. A new policy delta history is established once the policy is reapplied to the channel. Use the Start and End date filters to narrow your timeline to locate a specific delta, if necessary. Select a count under either FILES ADDED or FILES REMOVED to see a list of package files from a specific run.