- You’ll need to configure a Google Cloud project on GCP.
- You’ll need to enable the Google+ API for the project.
- You’ll need to create the credentials to use to authorize the platform to connect to Google IAM.
Enabling the Google+ API
With your project selected in Google Cloud Platform:- Select APIs & Services from the menu on the left.
-
Select ENABLE APIs AND SERVICES, then locate and select the Google+ API card in the API library.
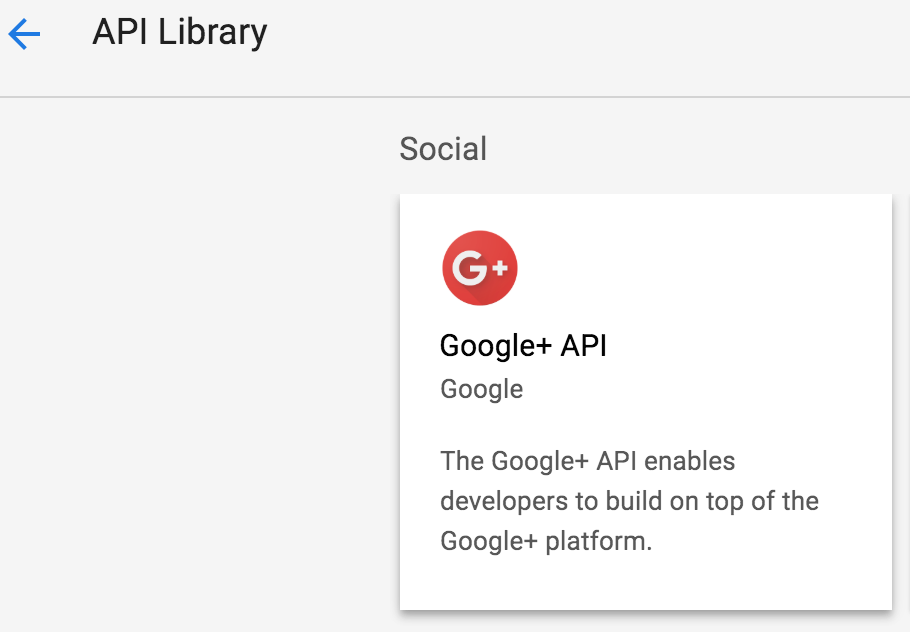
-
Click ENABLE.
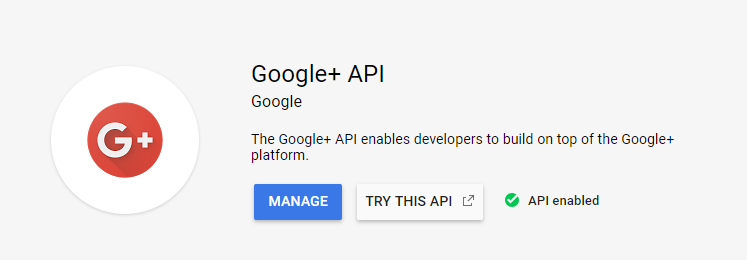
Creating Google+ credentials
With your project selected in Google Cloud Platform:- Select APIs & Services > Credentials from the menu on the left.
-
Click Create credentials and select Help me choose from the drop-down menu.
If you haven’t already, be sure to enable the Google+ API before proceeding.
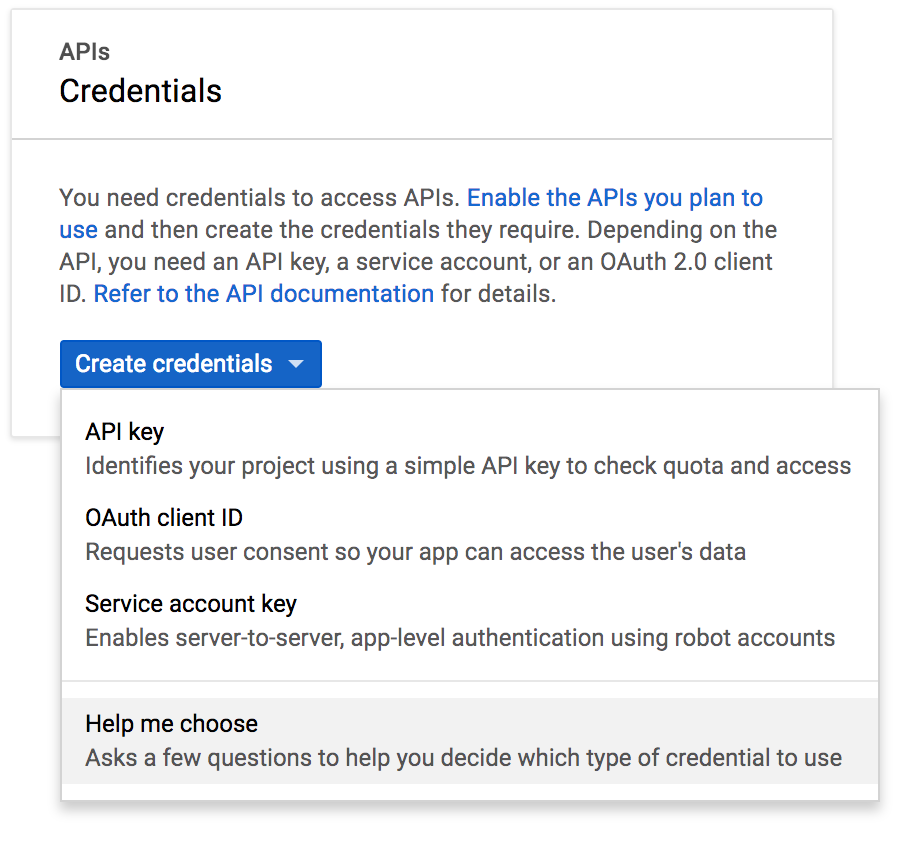
-
Select Google+ API from the API drop-down list, Web server from the next drop-down, and User data for the last question.
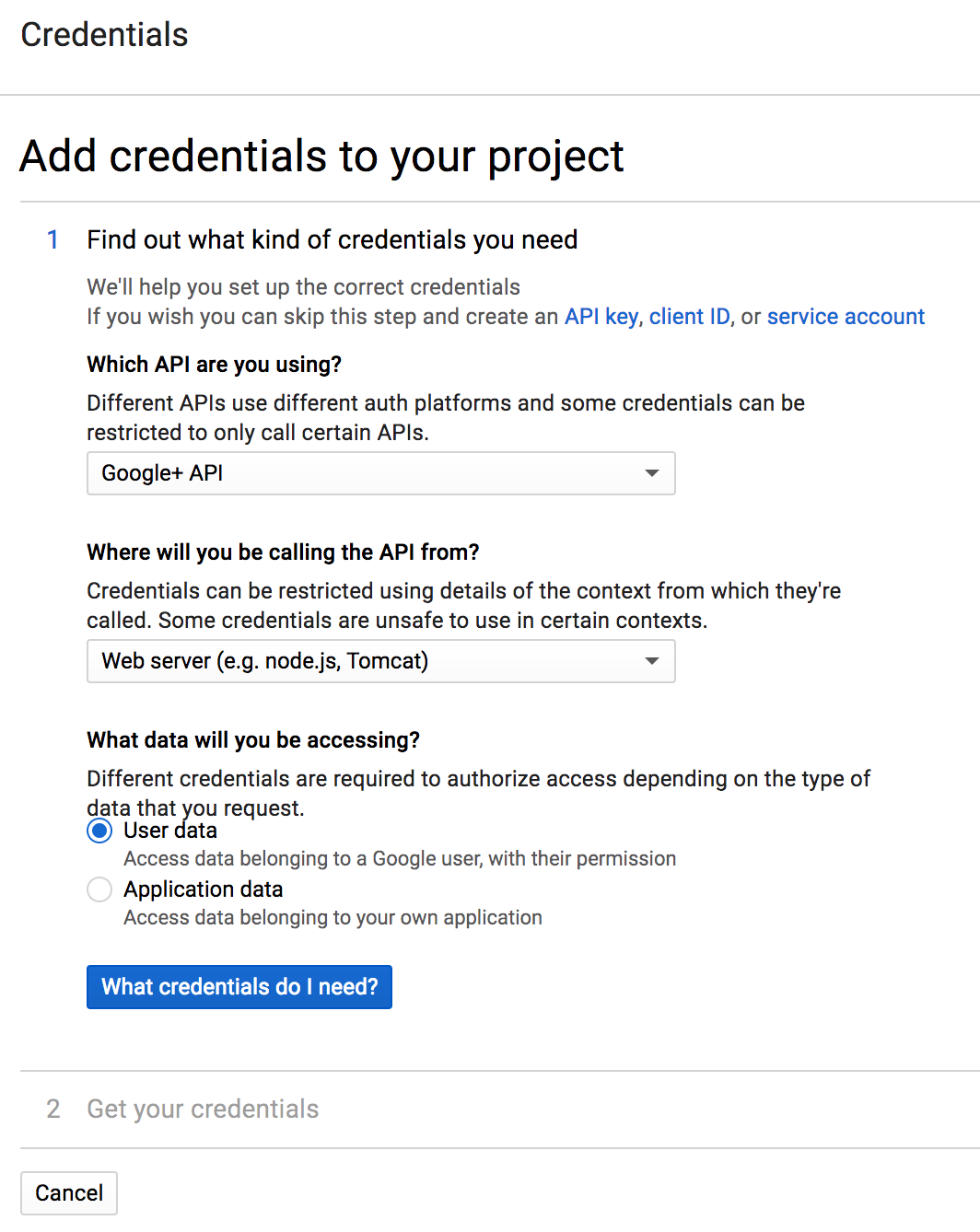
-
Click What credentials do I need? to create the appropriate credentials for the platform.
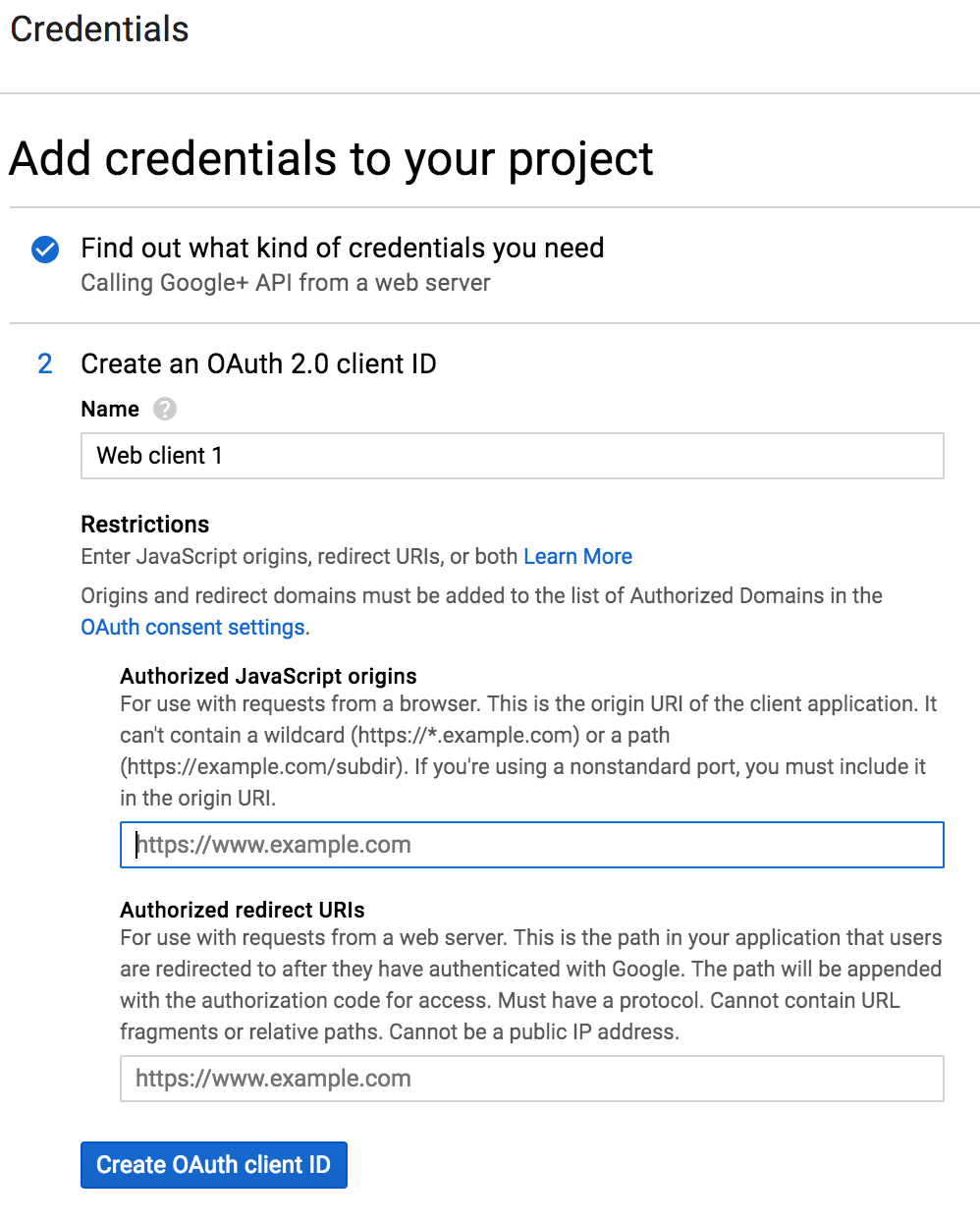
-
Enter a meaningful name, such as
Data Science & AI Workbench, to identify the platform (and help differentiate it from any other web applications you may have configured to use Google IAM). - In the Authorized JavaScript origins field, provide the FQDN of the Workbench server instance.
-
Open the Workbench Auth Center (see instructions below), and copy and paste the value from the Redirect URI field into the Authorized redirect URIs field here.
If the domain is not an authorized domain, you’ll see an
Invalid Redirecterror, and be prompted to add it to the authorized domains list before proceeding. - Click Create OAuth client ID.
-
On the OAuth consent screen tab:
- Set the Application type to Public.
- Set the Application name to
Data Science & AI Workbench(or something else meaningful to platform users). - Optionally, upload a logo to help users recognize Workbench.
- Provide a Support email address for users to reach out for help.
- Provide the full path to the authorized homepage where users will access Anaconda Enterprise.
- Optionally provide authorized links to a your organization’s privacy policy and terms of service.
- Click Create to display the OAuth client credentials that you’ll need to copy and paste into Workbench, to enable the platform to authenticate with Google. (See Step 5 below.)
Configuring Google to be your identity provider
Now that you’ve configured your GCP project to work with Workbench, you need to use the Workbench Administrative Console’s Authentication Center to configure Google as your external identity provider:- Open the My Account dropdown menu and select Admin Console.
- Select Manage Users to access the Keycloak user interface (UI).
- Log in using your Keycloak admin account credentials.
- Select Identity Providers from the left-hand navigation, then select
Googlefrom the Add provider dropdown. - The Settings tab displays the Redirect URI you need to copy to the Google Cloud project’s configuration. The Redirect URI will looking similar to this:
https://<full-qualified-domain-name>/auth/realms/AnacondaPlatform/broker/google/endpoint. - Copy and paste the credentials from GCP (Step 9 above) into the Client ID and Client Secret fields, and click Save.
When users choose this option and log in to the platform, they’ll be automatically added as new Workbench users. As an Administrator, you can then configure their group assignments and role mappings. For more information, see Roles and groups.